this post was submitted on 24 Mar 2025
11 points (100.0% liked)
Cybersecurity
6867 readers
111 users here now
c/cybersecurity is a community centered on the cybersecurity and information security profession. You can come here to discuss news, post something interesting, or just chat with others.
THE RULES
Instance Rules
- Be respectful. Everyone should feel welcome here.
- No bigotry - including racism, sexism, ableism, homophobia, transphobia, or xenophobia.
- No Ads / Spamming.
- No pornography.
Community Rules
- Idk, keep it semi-professional?
- Nothing illegal. We're all ethical here.
- Rules will be added/redefined as necessary.
If you ask someone to hack your "friends" socials you're just going to get banned so don't do that.
Learn about hacking
Other security-related communities [email protected] [email protected] [email protected] [email protected] [email protected]
Notable mention to [email protected]
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
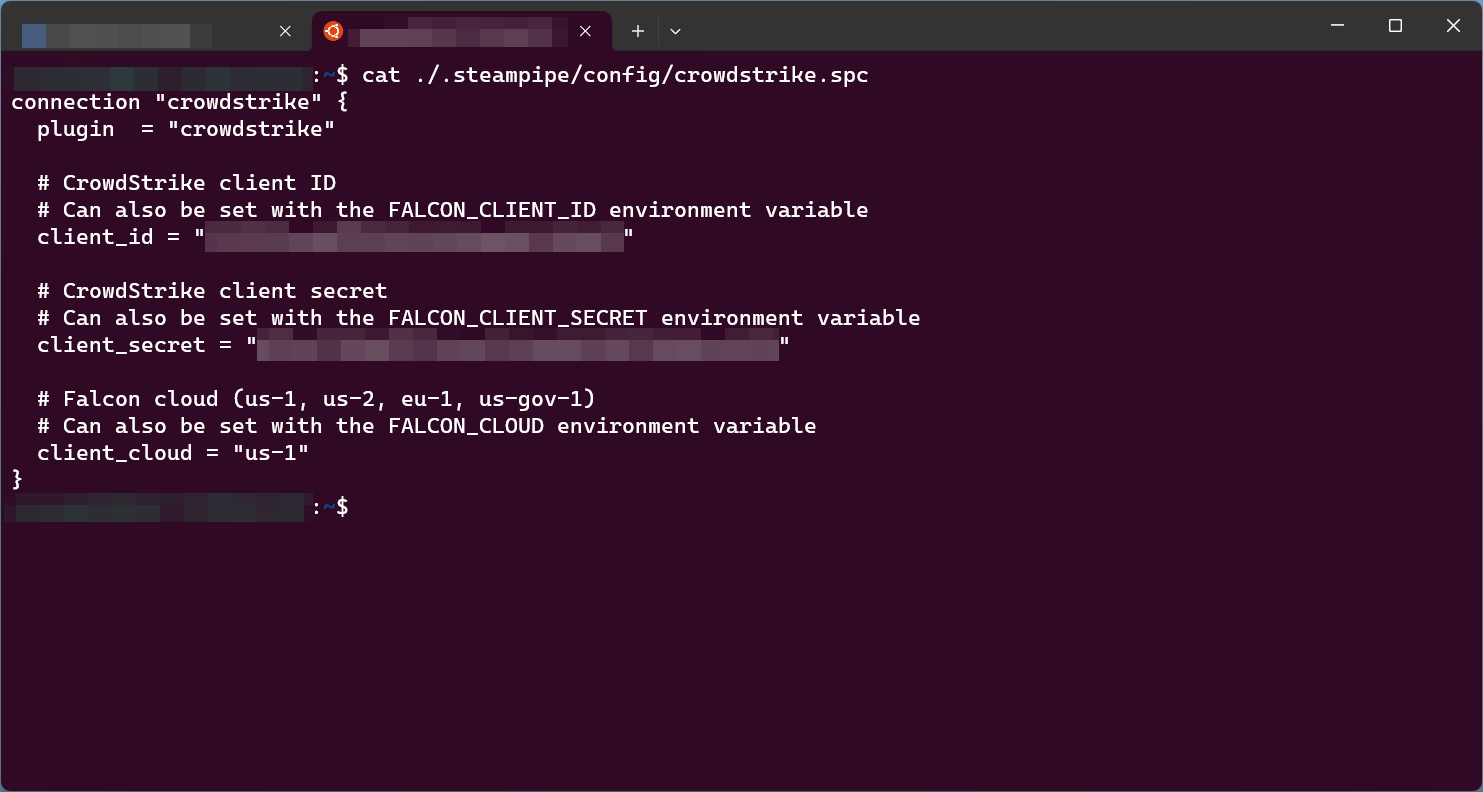
Yea it's a good complement to those tools too, but for plain compliance mods, use ~~flowpipe~~ powerpipe. Steampipe is more of a realtime view of resources, where wiz and orca are more scanners with state. You can kind of mimik it with steampipe but it's a lot of extra work. Credentials handling is entirely dependent on the plugin being used. So use a wrapper to pull whatever info from your secrets store (vault, sops, etc) and inject it in your local env/configs
I really appreciate the feedback. Thank you.