this post was submitted on 24 Mar 2025
11 points (100.0% liked)
Cybersecurity
6803 readers
64 users here now
c/cybersecurity is a community centered on the cybersecurity and information security profession. You can come here to discuss news, post something interesting, or just chat with others.
THE RULES
Instance Rules
- Be respectful. Everyone should feel welcome here.
- No bigotry - including racism, sexism, ableism, homophobia, transphobia, or xenophobia.
- No Ads / Spamming.
- No pornography.
Community Rules
- Idk, keep it semi-professional?
- Nothing illegal. We're all ethical here.
- Rules will be added/redefined as necessary.
If you ask someone to hack your "friends" socials you're just going to get banned so don't do that.
Learn about hacking
Other security-related communities [email protected] [email protected] [email protected] [email protected] [email protected]
Notable mention to [email protected]
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
It seems you have a lot of experience with the tool. Can you recommend any resources that teach more advanced use cases and configurations? I'm finding that just reading the docs, playing with it, and watching the YouTube videos I found aren't really doing it for me. Most of the materials I'm finding are about AWS, but that's not relevant to me.
Sorry, I don't. I learned by using. It's like any other tool, play with it, and look at the code and docs. What's your use case? From the sound of it, it's more a config managment issue than steampipe issue. I can try and help. Also they are active on slack and respond to bugs pretty quick in my experience.
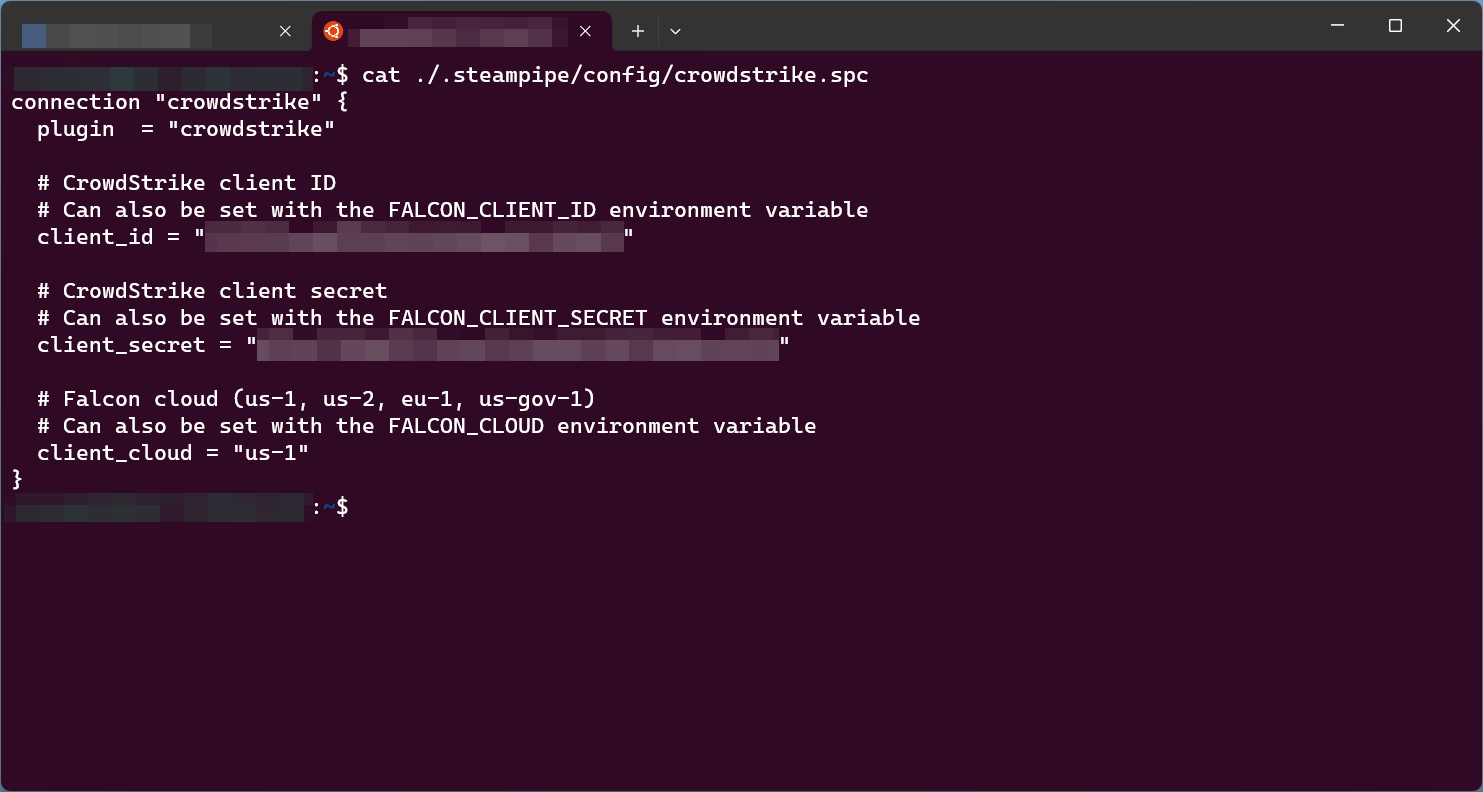
I saw someone mention it as an alternative to using Orca or Wiz for compliance use cases. I just wanted to check it out. I was attempting to run it locally rather than as a service with configuration via pipeline.
Sorry I'm new to lemmy, didn't see the screenshot, Yea if it's static creds locally I would use something simple like 1pass or sops and just make a wrapper to pull the data (after authenticating) and populate the needed environment variables. But if you have multiple connections with the same plugin it won't work. So you need to get creative on setting up per connection settings. Usually for that it's still stored in a secure storage but the config is rendered on startup using some simple bash or templating. The real advantage of steampipe for me is the aggregated connections, searching all Aws accounts for a resource Or dumping all r53 records with a simple query is a godsend. And adding tooling like redash make it even easier to drill down and share data
Yea it's a good complement to those tools too, but for plain compliance mods, use ~~flowpipe~~ powerpipe. Steampipe is more of a realtime view of resources, where wiz and orca are more scanners with state. You can kind of mimik it with steampipe but it's a lot of extra work. Credentials handling is entirely dependent on the plugin being used. So use a wrapper to pull whatever info from your secrets store (vault, sops, etc) and inject it in your local env/configs