This was made possible by a validation error in Microsoft code
lol microsoft
Banned? DM Wmill to appeal.
No anti-natilasm posts. See: Eco-fascism Primer
Vaush posts go in the_dunk_tank
This was made possible by a validation error in Microsoft code
lol microsoft





What can they do with a signing key?
Leak Hillary Clinton Emails
delicious buttery mails
Pretend to be someone they aren't
An actor that can acquire a private signing key can then create falsified tokens with valid signatures that will be accepted by relying parties. This is called token forgery.
Oh cool so they can distribute updates?
The article just says they signed authentication tokens which gave them access to outlook emails. I don't think it was code signing that would let them distribute software, and that's not what they were after.
Thanks for actually reading the article o7
Is that hacker news over telegram?
I really struggle to believe that a military performing espionage actions is stupid enough to operate without spreading hours of operation in a harder to track way. But maybe they don't give a shit? Just seems like something you could easily hide.
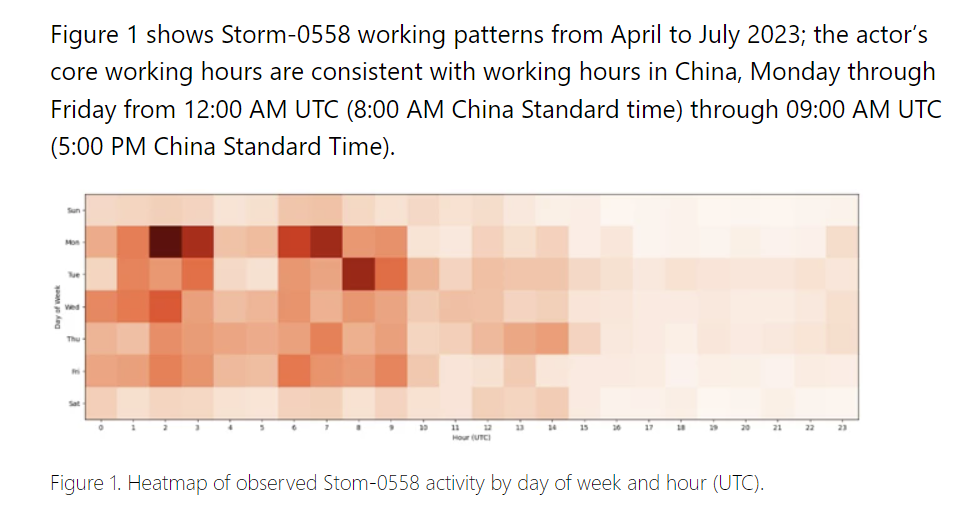
EDIT: Question - Why would an inactive microsoft consumer account have the ability to forge tokens for Outlook.com? Would this not limit it to a specific subset of accounts?
We determined that Storm-0558 was accessing the customer’s Exchange Online data using Outlook Web Access (OWA).
Ahh yes, this would be one specific customer of microsoft that was targeted. Hopefully the NSA or some shit lmao
Really makes you think
Yeah you can go full conspiracy brain with this if you want to question whether microsoft and the state would collaborate for propaganda. I'm not quite so tinfoil hat but there's certainly questions.
Calling everything potential Inter-intel-agency warfare is my favorite new tinfoil one-upmanship move
The more things deteriorate the more sus everything everywhere looks.
I have just skimmed this so maybe it's answered, but seems the entire thing boils down to:
Storm-0558 acquired an inactive MSA consumer signing key
How?