This all kind of depends on your threat model... a VPN hides traffic from your ISP, and puts your traffic in with a lot of other traffic, but domestic IPs generally rotate fairly frequently, so only your ISP really knows when that happens, but they also probably sell that data because we live in an over-financialized, under-regulated hellscape, but your VPN also exists in that hellscape, and knows who you are just as much unless you buy Mulvad with perfectly laundered monero and is as likely to be selling that data if not more so than your ISP. There's a reason why people use tor...
Privacy
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn't great, if contents of the website are behind a paywall maybe copy them into the post
- Don't promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
much thanks to @gary_host_laptop for the logo design :)
Thx
As some have stated depends on treat model. I personally use Mullvad for both pirating and accesing restricted sites in my country and evading shity laws. 5€ 5 devices with no bottleneck it's pretty good. Sometime I use tor when I try to reach a site that the WiFi provider has blocked
The problem with Mullvad is that there is not port forwarding for seeding stuff
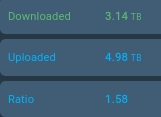
There's no problem with seeding. There's actually more uploaded than downloaded
not working quite that well on my end. no matter how popular torrent, mine won't seed at all. and i can't download some rare ones where there's like less than 50 seeds.
What OS are you using? App? If you're using qbittorent make sure you have selected tun in advanced -> network interface
My bad
If you are really concerned, buy VPC from large cloud provider, install HTTPS server proxy, configure your web browser to use it. 512MB RAM server will be sufficient as long as it is given enough CPU. Free google instance is suffering from low CPU, not memory.
This way your link between you and internet provider is obscured. Your IP will be shared with others by cloud provider, so you get some obfuscation on that end.
If you use your own certificate authority, then you will get 100% man in the middle protection for link between internet provider and your home. If you use let’s encrypt, then we don’t know that status.
Advantage of this model is speed.
Your browser is still finger-printable, as always.
Securing DNS is its own topic.
You shifted your identity to cloud provider, so it is never 100% safe.
Forget about we keep no logs VPN statements. Judge order and you are logged by VPN provider and don’t know it. So what are you paying for? Slow speed and obfuscation of IP?
Or maybe a two hope vps setup should be great too, while preserving usable speeds
Depends on your threat model - mine is to make it as annoying and difficult for data sellers and advertisers to profile me as possible so in that scenario a reputable VPN service makes perfect sense.
There's no such thing as total privacy and each service/software is simply a piece of the puzzle. If my government really wanted my data I'm sure they could find a way but making it as difficult as possible for techno-fascists is fine by me.
Privacy is a trade-off against convenience, and there is no perfect privacy.
VPNs are a mediocre privacy tool, because they presuppose trust in the VPN provider. Tor is flawed because it is open to correlation attacks.
There are low-hanging fruit that everybody should be using like sensible cookie policies, HTTPS-only mode, and DNS over HTTPS.
If you are looking for a solution on the far end of privacy/inconvenience you could look into I2P and use that situationally.
I would rather put my trust in a good VPN provider than the big CAs. And HTTPS only and DoH is not going to protect you from fingerprinting using your IP address.
Is a self hosted VPN good for daily privacy?
That depends on your threat model. It's a useful strategy to hide your traffic from your local network admin (e.g. at the workplace) and your ISP, but it's a bad strategy for hiding your identity from the sites you're visiting.
In my opinion, a VPN is a must-have, especially if you’re self-hosting, especially for a media server.
What does VPN hide that HTTPS can’t hide for media server?
I am looking at the scenario of listening to my music collection on self-hosted Jellyfin server.
IP address of my phone? That’s irrelevant.
HTTPS is way faster than VPN.
VPN into your home lab isn't about privacy, it's more about reducing your exposed services to the public internet.
If you have only the ports needed to VPN back into your network, then the rest is hidden behind your router. You only need to fully secure one thing, instead of having to ensure that everything is 100% patched.
It's not the only thing you should be doing, but it does help reduce the probability of a breach.
What does VPN hide that HTTPS can’t hide for media server?
HTTPS Doesn't hide where the traffic is going, so your ISP will track you going to piracy sites. It also doesn't protect you against identification when torrenting.
I use a VPN but you might look into portmaster and their spn. Its a little slow but even using portmaster without the spn you can filter your traffic and simply deny most apps access to the internet
Will look at it