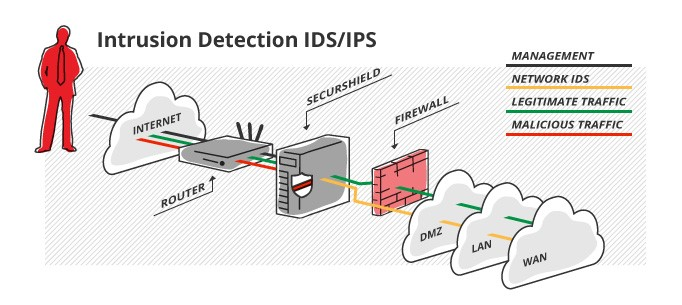
Not professional sysadmin. I run my homelab and handles a few servers at work. I don't use IDS. So may be irrelevant.
- WAF to stop HTTP parameter pollution and request smuggling
- Fail2ban on SSH and move ssh away from port 22
- Setup LAN recursive resolver and disallowed outbound raw DNS
For me, a lot more emphasis is on defending the application
- Setup systemd unit hardening
- Use Landlock LSM to whitelist directories (modifying source needed). Stops directory traversal and command execution
- TLS or
stunnelbetween application and database - Point DNS to local resolver
- LD_PRELOAD hardened allocator
I'm currently looking into the Linux port of pledge to further reduce post exploit attack surface. But the project is not mature enough for production, yet.