cross-posted from: https://programming.dev/post/36575333
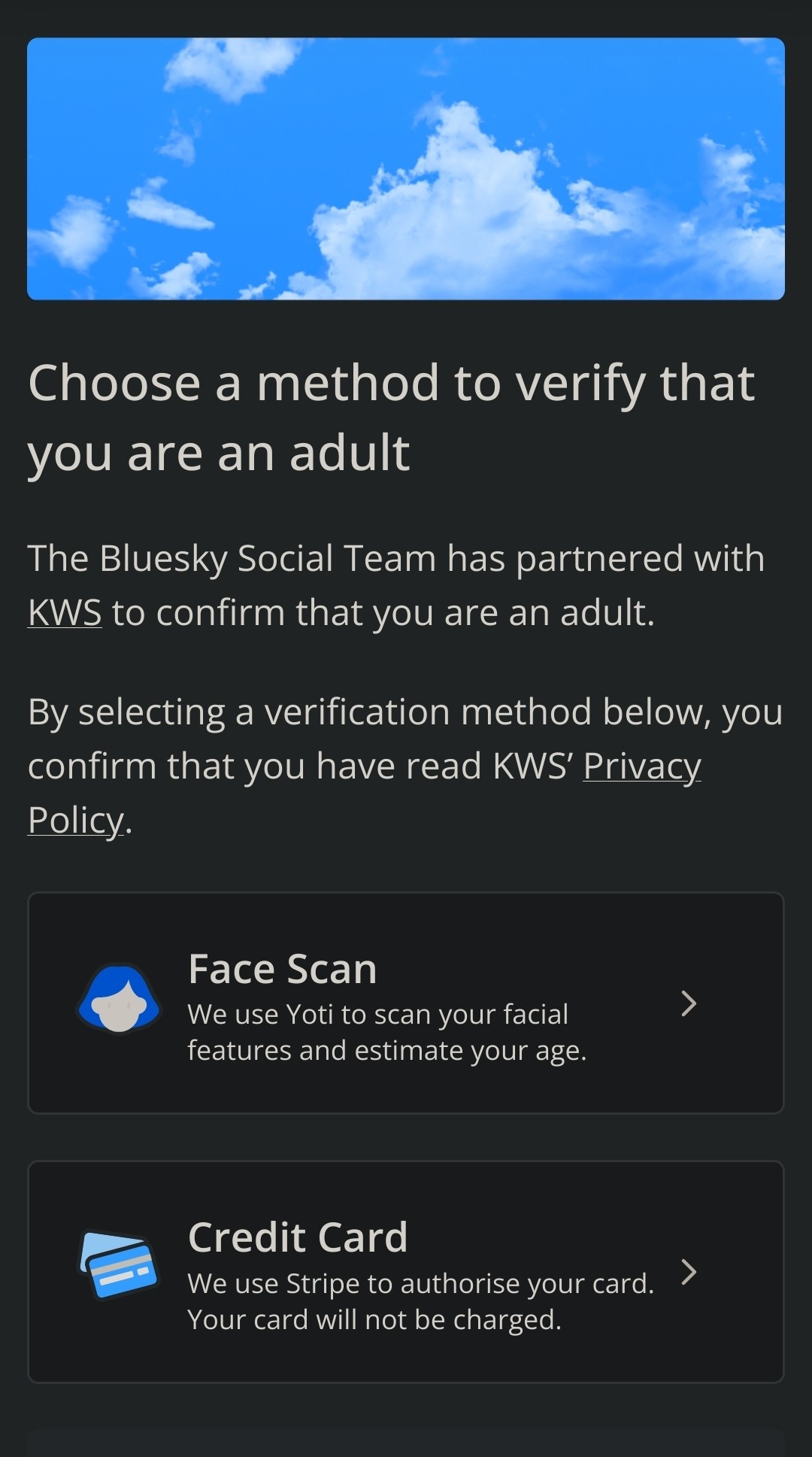
Property technology broadly refers to the use of software, digital platforms, and other digital tools used in the housing market. Property owners and renters use these technologies for functions including advertising, touring, leasing, and financial management of rental housing. These tools may incorporate computer algorithms and artificial intelligence.
Selected Property Technology Tools Used in Rental Housing
Property technology tools used for advertising, tenant screening, rent-setting, and facial recognition have both benefits and risks. For example, facial recognition technology can enhance safety, according to three industry associations and all 10 of the public housing agencies in GAO's review. However, these tools also may pose risks related to transparency, discriminatory outcomes, and privacy. For instance, potential renters may struggle to understand, and owners to explain, the basis for screening decisions made by algorithms. Facial recognition systems also might misidentify individuals from certain demographic groups, and property owners might use surveillance information without renter consent, according to advocacy groups GAO interviewed.
The four federal agencies took several actions to address these risks. To combat alleged misleading and discriminatory advertising on rental platforms, agencies pursued legal action and obtained settlements requiring changes to advertising practices and improved compliance with the Fair Housing Act. They also took enforcement actions against tenant screening companies for using inaccurate or outdated data.
However, all 10 public housing agencies stated public housing agencies would benefit from additional direction on use of facial recognition technology. The Department of Housing and Urban Development's (HUD) current guidance to these agencies is high-level and does not provide specific direction on key operational issues, such as managing privacy risks or sharing data with law enforcement. More detailed written direction could provide public housing agencies additional clarity on the use of facial recognition technology and better address tenant privacy concerns.