politics
Welcome to the discussion of US Politics!
Rules:
- Post only links to articles, Title must fairly describe link contents. If your title differs from the site’s, it should only be to add context or be more descriptive. Do not post entire articles in the body or in the comments.
Links must be to the original source, not an aggregator like Google Amp, MSN, or Yahoo.
Example:
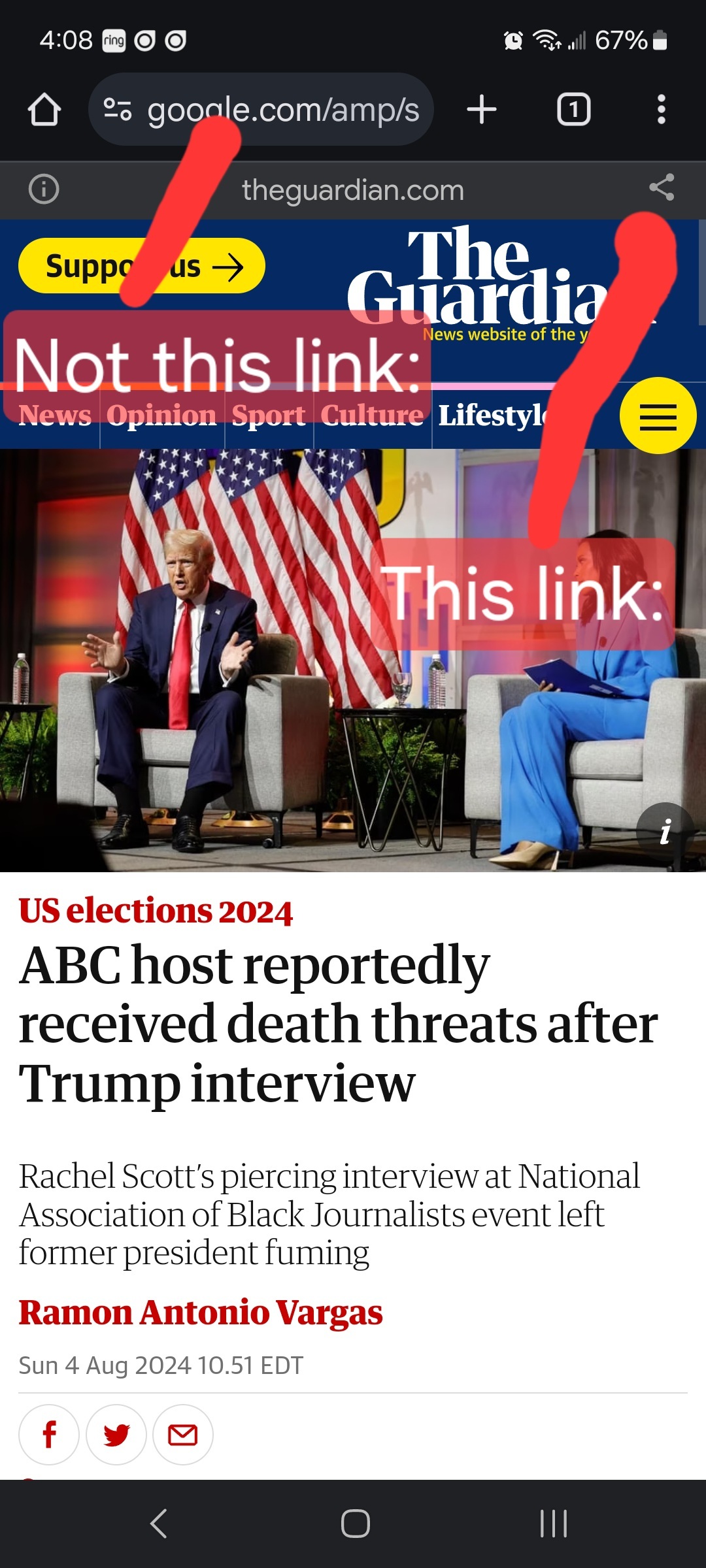
- Articles must be relevant to politics. Links must be to quality and original content. Articles should be worth reading. Clickbait, stub articles, and rehosted or stolen content are not allowed. Check your source for Reliability and Bias here.
- Be civil, No violations of TOS. It’s OK to say the subject of an article is behaving like a (pejorative, pejorative). It’s NOT OK to say another USER is (pejorative). Strong language is fine, just not directed at other members. Engage in good-faith and with respect! This includes accusing another user of being a bot or paid actor. Trolling is uncivil and is grounds for removal and/or a community ban.
- No memes, trolling, or low-effort comments. Reposts, misinformation, off-topic, trolling, or offensive. Similarly, if you see posts along these lines, do not engage. Report them, block them, and live a happier life than they do. We see too many slapfights that boil down to "Mom! He's bugging me!" and "I'm not touching you!" Going forward, slapfights will result in removed comments and temp bans to cool off.
- Vote based on comment quality, not agreement. This community aims to foster discussion; please reward people for putting effort into articulating their viewpoint, even if you disagree with it.
- No hate speech, slurs, celebrating death, advocating violence, or abusive language. This will result in a ban. Usernames containing racist, or inappropriate slurs will be banned without warning
We ask that the users report any comment or post that violate the rules, to use critical thinking when reading, posting or commenting. Users that post off-topic spam, advocate violence, have multiple comments or posts removed, weaponize reports or violate the code of conduct will be banned.
All posts and comments will be reviewed on a case-by-case basis. This means that some content that violates the rules may be allowed, while other content that does not violate the rules may be removed. The moderators retain the right to remove any content and ban users.
That's all the rules!
Civic Links
• Congressional Awards Program
• Library of Congress Legislative Resources
• U.S. House of Representatives
Partnered Communities:
• News
view the rest of the comments
Side note: I'd really like to know what evidence they have for stating that a country is "suspected". If the only reason is that traffic was routed through a countries IP addresses, then literally anyone anywhere can do that; otherwise it's essentially disinformation and they can "suspect" whomever is geopolitically relevant at any given time.
their methods are indeed significantly more sophisticated than that. explaining them accurately, however is beyond my knowledge… and i’m a principal engineer that deals with security quite regularly
They use different heuristics to make their best guess, and to give themselves a confidence score.
Some indicators include whether groups refuse to target certain targets, what time zones correspond with their highest activity levels, types of linguistic or grammatical markers they use, including grammatical errors (a native Russian speaker makes different types of English mistakes as a native Chinese speaker), keyboard layouts, types of punctuation, etc.
From there, watching their techniques can kinda reveal what other groups they might learn from or cross pollinate with.
Everything can be spoofed, of course, but maintaining a false persona for a long time is hard, and often not worth doing.
The best example of attribution I know of was the 2018 Winter Olympics. This was shortly after the Russian doping scandal. Russia basically made a press release and said "The Olympics is going to be hacked, people are going to blame us for it but it totally isn't us." The hack happened, and it bore some of the hallmark signs of Russian hackers. However, it also had signs of being Chinese and also North Korean. They basically used techniques from every major nation state hacking group to cover their tracks. In the end it was still pinned on Russia, because one of the command and control servers previously had an IP address used in a Russian cyber attack on Ukraine. The indictment was also juicy, the US called the hacking group "petulant children".
There's a Darknet Diaries episode that covers it and goes into more detail:
Darknet Diaries: 77: Olympic Destroyer
Episode webpage: https://darknetdiaries.com/episode/77
Media file: https://www.podtrac.com/pts/redirect.mp3/dovetail.prxu.org/7057/290978c7-55c1-43df-ac19-2cb89f96994d/b5a200ec-adad-431b-b227-c2c1dfdb01f8.mp3