Yo dawg
iiiiiiitttttttttttt
you know the computer thing is it plugged in?
A community for memes and posts about tech and IT related rage.
Perfect Security. Nobody gets in.
False positives are way more important to prevent than false negatives anyways.
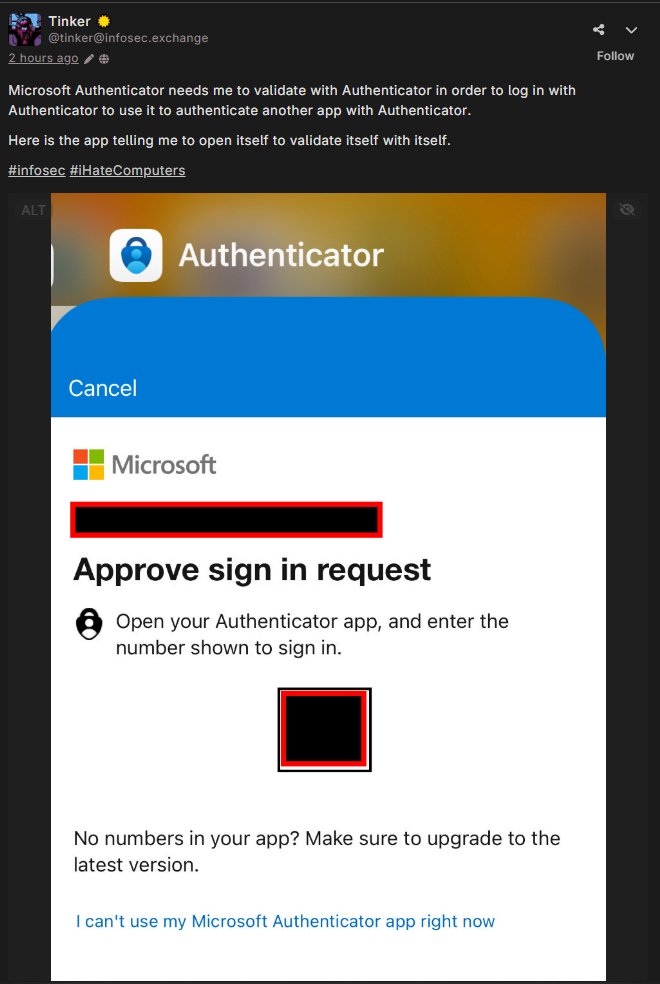
Pretty sure you have another device registered with Authenticator here, and it is asking you to verify against that.
It would be bad if somebody could just steal your username/password and then register their own MFA, right?
So i recently had this happen. I set up Microsoft authenticator on my phone, found out our IT team wants us to use Google authenticator for some reason, hit the disconnect from device button... And got an infinite loop of being redirected to the Microsoft app, and clicking the "cant access" button brought me back to... The Microsoft authenticator app.
Had to ask IT to delete my 2fa on their end and try again.
thanks for claryfing that, it makes the post really dumb
This is a legit problem with authenticator. My work phone was wiped and I had to have my authenticator reset because it got stuck in the same loop.
Well, if the MFA device is not available, reset is the only way. If user would be able to bypass the lost device, the whole thing would be vulnerable.
Whole MFA is of course really f stupid, but it is best we got against phishing.
This happens when your Microsoft account password is externally managed by your employer. If the password is changed externally, then authenticator needs to re-authenticate… with itself.
Keeper does the same. Because that's sane security.
Lemmy: $MS dumb and bad! (Please clap.)
If we're headed into a chaotic and terrible time of uprising and war these next few decades, I hope among the things that get shelled and flattened, all of Microsoft's offices are among them. It would be a shame if, like IBM nearly a century ago, Microsoft remains in the aftermath.
https://mysignins.microsoft.com/security-info
Obviously it's very fashionable to bang two saucepans together while chanting "microsoft baaaaad", but for anyone interested in actually learning about how this stuff works: Authenticator will never use 'itself' to authenticate, but you can use a second, seperate instance of Authenticator on another device to authenticate which is what is happening here. If you use Entra (or whatever it's called this week), go to that URL to see which MFA methods Microsoft thinks you have and if, say, there's a copy of Authenticator on a phone you no longer own, or an outdated phone number, or whatever, you can delete it.
Nothing in the UX here conveys that you should open a second Authenticator on a second device. And what if you aren’t logged into the second Authenticator? Is a third one needed on a third device? And if you aren’t logged into the third?
The original TOTP phone apps don’t require their own login. The protection is provided by the mobile OS.
Microsoft is making this complex it’s not usable.
MS Authenticator also uses the phone's built-in security and can also be used for plain TOTP without sign-in if you want. If you aren't signed in on a separate instance it won't offer Authenticator as an option. I think a reasonable person would have realised that based on my answer or, if you were really interested in finding out, from the documentation but I guess you bought those saucepans so you might as well use them. I suppose you're right in a sense; if Microsoft really wanted to make the UX idiot-proof they'd have a link that says something like "I can't use my Microsoft Authenticator app right now."
Out of interest, what happens if you lock yourself out of the completely free, open source and self-hosted app that has your TOTP codes? What recource would you have that isn't also true for MS Authenticator, or Google Authenticator, or any of the other ones?
For work apps, you can “contact an admin” if you can’t access TOTP. Some other services also have account recovery options if you lose that access.
In other cases, I think you are screwed because you opted into requiring a second factor then lost it.
or request/get a keyfob for the 2nd authentication?
had to do that shit at my last job. and although tedious, it was better than installing an MS app on my phone
Currently doing an internship at an establishment with 1300+ users using Microsoft authenticator (required by policy). The amount of times I've had this same issue is insane. Worst part is, when we provision someone with a new company phone, they have to go to the Google play store to download Microsoft authenticator. The play store however, requires a google login to download apps, but the users cannot log in to their company Google account without authenticator, creating a circular dependency. This unintentionally means every employee HAS to have a personal google account to set up their company google account... Stupid as hell.
Why not just install the Authenticator APK some other way initially? Just give people a download from some random server you control.
Logically it should be perfectly fine to install authenticator app on a personal device, if that suits the user. 2FA adds security to the password, but the password itself is not meant to be known by anyone else, including any other employee or any other company owned device.
Also, you can enroll mobile devices to Intune and have the authenticator app installed before the employee receives it.
I just switched to aegis when authy went to light mode. I like it.
One of the main feature of MS Authenticator is native integration with the MS authentication system. Aegis doesn't have such integration
That's kind of the point...
The less of their stuff I have in my life, the better.
funny to me when people are like "I need that integration to automatically approve all auth requests because typing that six digit number in is JUST TOO MUCH MAN!!!"
That sounds like a bug in waiting honestly. I don't trust Microsoft that much

This isn't a Microsoft issue. This is a stupidity issue. Any authenticator you add 2 factor to, and then put the 2 factor in that same app will do this.
Even better/worse, Microsoft will never send 2FA requests to the app that is requesting them. This user has a second copy of Authenticator installed somewhere else which they forgot about.
in a sandbox or VM? or perhaps a rooted phone which does all that and more.
Oh that's reassuring, I thought maybe it was just because I'm using it on Huawei.
This is why I hate passkeys and authenticators (as mandatory requirements). The moment I lose my phone I’m just completely fucked with no recourse, in actual use case.
You're supposed to have backups for MFA. Though for passkeys (specifically ones for yubikey) are really hard to backup.
I am not always going to remember to register my primary yubikey and my two backups that are physically never together.
I use andOTP for two factor authentication. It's free and open source, and available from the F-Droid app store. It allows you to backup your cryptographic keys in plaintext, with a password, or asymmetrically encrypted using OpenPGP. I keep my backups in a fireproof safe on two flash drives.
Thank you for the resources, I’ll be sure to check them out.
Unfortunately I’m still on iOS atm (hoping to switch to Android -> GrapheneOS down the line, when I have the finances), so I’m stuck trying to find something that’ll work between that and my Linux desktop, with GoogleAuth being my primary OTP app.
Cursory Internet search suggests something called 2FAS for mobile so I’ll see if it’s a cross platform option. I actually didn’t know non-corpo authenticators existed until today so it’s an exciting path to explore. /gen /pos
Yeah I had a beautiful moment trying to use Google's find my phone feature in another country when it asked me to use MFA on...my fucking phone. Turned off Google MFA forever after that near nightmare. Luckily another kind tourist found and turned in my phone to the nearest worker at the place I was visiting
I broke my phone, and this actually happened to me. Google had set my old broken phone as a default passkey without my knowledge, back when they were rolling it out. My sim card was retrievable, so I used SMS to get in after my password. Turns out, that's not good enough. It took me days to get into my idiotic accounts (including Google authenticator for work) because of all the security hoops, even with backup codes, password managers, and a SIM card.
My saving grace was Firefox Sync, which allowed me to get into Microsoft accounts and slowly start unwinding Google's insane requirements.
Seems like someone took DRY too far…
The authenticator itself is not supposed to use the same auth dialog than everything else 😅
Nothing says Microsoft like a bit of janky paradox.
There are plenty of FOSS authenticator apps that can authenticate Microsoft account hassle free. I have been using one for years now.
I had an issue with this a few weeks ago, my old phone the charging port broke and I couldn’t get back into it. On my new phone it needed me to use the authenticator to log in to the authenticator. Made it my uni’s problem to solve the authenticator paradox
It's a security feature.
If it was easy to get into without the authenticator, then it would be useless.
*laughs in Okta*